The logon interface is one of the most used interfaces in Windows computers, yet it is also one of the most ignored attack vectors. In this post I would like to share some documented and undocumented tweaks to harden the Windows 11 logon interface.
Please note that although the article only focuses on Windows 11 for the sake of conciseness, there were not any major changes to logon experience in Windows 11, so the behavior should be the same in Windows 10 as well. The following content was tested on Windows 11 Pro/Enterprise version 21H2.
In general, local attack vectors are not taken that seriously since there are multiple challenges the threat actors need to go through before such attacks even become feasible. Although threat modeling makes certain risks acceptable, a good defense-in-depth approach should try to harden each domain independent from each other without assuming prior security layers would stop the problems specific to the current layer.
Authentication
The primary purpose of a logon program is to authenticate users, and authentication is simply the process of determining whether a user (or other entity) should be allowed access to a system
or the question of Are you who you say you are?
and we determine that by verifying a single or combination of three factors [1]:
- Something you know
- Something you have
- Something you are
When you combine two or more of these, it is called multi-factor authentication, having to enter a secure PIN that is sent to your phone via SMS or generated by an authenticator app and that changes every time after logging in with a username and a password is one of the most popular ways to do it (i.e., something you know + something you have). Something you are
has become more prevalent in the recent years with fingerprint readers and depth-aware cameras that allow a more accurate capture of faces becoming more available on mobile devices. Whether it is single or multi-factor, neither of these techniques are superior to one another, and their best use case depends entirely on one’s threat model, and it is not the main topic of this article. This article is simply about hardening the logon interface itself.
Analysis
This is how Windows 11 logon interface mostly looks like out of the box:
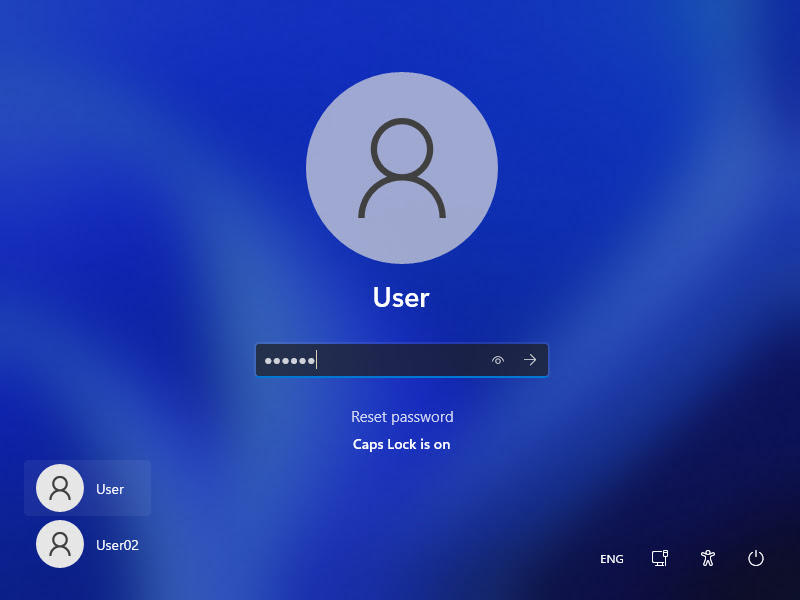
Windows 11’s default logon interface
We can see that there are multiple UI elements that don’t have anything to do with authentication process:
- Language selection widget
- Network selection widget
- Ease of Access widget
- Power options widget
- List of usernames
- Background image
- Account picture
- Reset password button
Obviously determining if a feature is a security risk -again- highly depends on individual threat model. But for my threat model, an user should not be able to interact with language selection, network connection, power options, ease of access utilities (which is a known vulnerability since Windows XP times) and anything else without authenticating themselves. Let’s say there is a critical process running in the background, an attacker or a clumsy user can cause a Denial-of-Service attack by disabling the network connection or shutting down the computer. I know that they can just unplug the power connection, but this is what defense in depth is about, always have secondary and even tertiary measures in place, just in case.
Besides what is visible in the screenshot, there are also some other areas that is open to further hardening:
- Before the logon interface, there is also another program running called the lock screen that becomes visible once the screen is locked and which shows background images. But most importantly it has read access to some native apps such as Calendar, Mail, and Weather depending on how the user has personalized it. Read access to application data should be only given to authenticated and authorized users.
- It is possible to mute, unmute or change the volume with the volume controller key on the keyboards. Realistically, this is not really a security problem, but technically only an authorized user should be able to modify the volume or be given execute access.
- On non-Server Windows systems, Secure Attention Sequence (SAS) is not enabled for the logon interface by default which potentially allows a non-privileged attacker to display a fake logon interface to capture the credentials. I will share more information regarding SAS in the next section.
Hardening
Logon interface
Fortunately, Microsoft has some documentation available to customize the logon interface for vendors who wish to customize their Windows installations.
On Windows Enterprise systems, it is possible to disable the Power, Language and Ease of Access buttons on the logon interface by setting the BrandingNeutral DWORD registry value in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Embedded\EmbeddedLogon according to the table below [2]:
| Action | Hexadecimal value |
|---|---|
| Disable the Power button | 0x2 |
| Disable the Language button | 0x4 |
| Disable the Ease of Access button | 0x8 |
| Disable all Welcome screen UI elements | 0x1 |
You can just set it to 0x1 if you wish to disable all three buttons or you can XOR the value of the items that you wish to disable (e.g., Disable the Language button + Disable the Ease of Access button = 0x4 ^ 0x8 = 0xC).
And the network selection button can be disabled by setting the following group policy to Enabled: Computer Configuration > Administrative Templates > System > Logon > Do not display network selection UI [2]. Unlike the previous registry edit, this group policy also works on Windows 11 Pro systems as well.
I was unable to find any tweak to disable the Reset password
button itself which only appears after entering wrong credentials. Normally, once pressed, it asks the user the answers for their security questions to reset the password. However, if you set the Computer Configuration > Administrative Templates > Windows Components > Credential User Interface > Prevent the use of security questions for local accounts group policy to Enabled, it will instead display an error message that states This feature requires removable media, such as a USB flash drive. Please connect a USB flash drive, and then try again
[3] which is referring to the password reset disk that should be created while logged in as the user whose password is being reset.
To disable the list of usernames being visible during signing in, change the Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options > Interactive logon: Don’t display last signed-in group policy to Disabled.
For some threat models, interface customization might not be desired. To disable the logon screen background image, change the DisableLogonBackgroundImage DWORD registry value in HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System to 1.
Unfortunately, I was unable to find an effective way of disabling the account picture UI element. It is possible to disable it by setting it to a blank transparent picture but that does not really count, does it?
Finally, accessing the volume controls with keyboard while not logged in can be disabled by setting the EnableLogonHIDControls DWORD registry value in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Audio to 0.
Here is how Windows 11 logon interface currently looks like with redundant UI elements disabled. Much better.
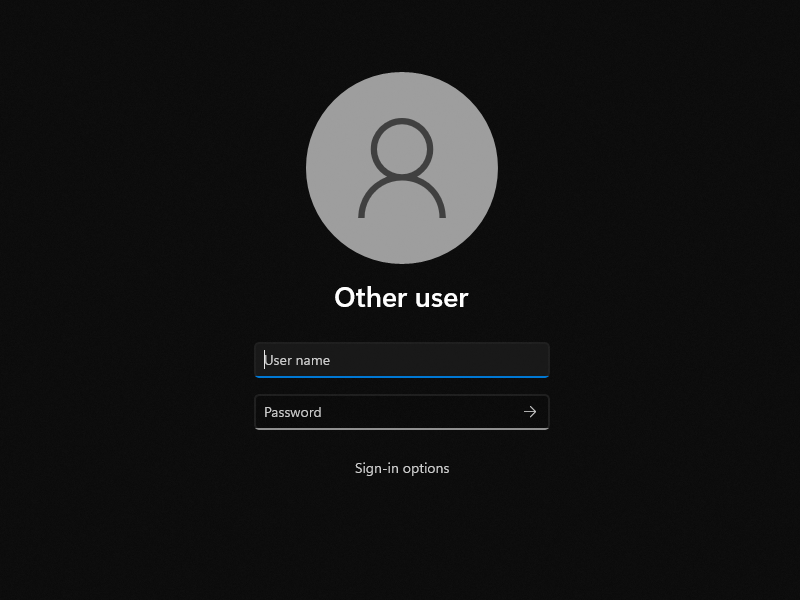
Windows 11’s logon interface during sign-in with redundant UI elements disabled
Lock screen
Lock screen can be disabled by setting the Computer Configuration > Administrative Templates > Control Panel > Personalization > Do not display the lock screen group policy to Enabled. That way you won’t have to press a key to bring up the logon interface whenever you lock your screen or before you sign in.
However, having to press a key before the logon interface is not necessarily a bad thing. In fact, if the key sequence in question is CTRL + ALT + DEL, it is a Good Thing™ because this specific key sequence is known as Secure Attention Sequence or SAS, and it is used to harden the system against login spoofing. Quoting from Windows Internals [4]:
How SAS is implemented
The SAS is secure because no application can intercept the Ctrl+Alt+Del keystroke combination or prevent Winlogon from receiving it. Win32k.sys reserves the Ctrl+Alt+Del key combination so that whenever the Windows input system (implemented in the raw input thread in Win32k) sees the combination, it sends an RPC message to Winlogon’s message server, which listens for such notifications. The keystrokes that map to a registered hot key are not sent to any process other than the one that registered it, and only the thread that registered a hot key can unregister it, so a Trojan horse application cannot deregister Winlogon’s ownership of the SAS.
A Windows function,SetWindowsHookEx, enables an application to install a hook procedure that’s invoked every time a keystroke is pressed, even before hot keys are processed, and allows the hook to squash keystrokes. However, the Windows hot key processing code contains a special case for Ctrl+Alt+Del that disables hooks so that the keystroke sequence can’t be intercepted. In addition, if the interactive desktop is locked, only hot keys owned by Winlogon are processed.
Once the Winlogon desktop is created during initialization, it becomes the active desktop. When the Winlogon desktop is active, it is always locked. Winlogon unlocks its desktop only to switch to the application desktop or the screen-saver desktop. (Only the Winlogon process can lock or unlock a desktop.)
This is the default behavior on Windows Server. For non-Server systems, it can be enabled by setting the Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options > Interactive logon: Do not require CTRL+ALT+DEL group policy to Disabled.
Now Windows 11 is going to ask the user to press Ctrl+Alt+Delete to unlock the lockscreen. If this prompt does not get displayed during the period where this policy is configured, it might be a good idea to be careful since it could be a login spoofing attempt.
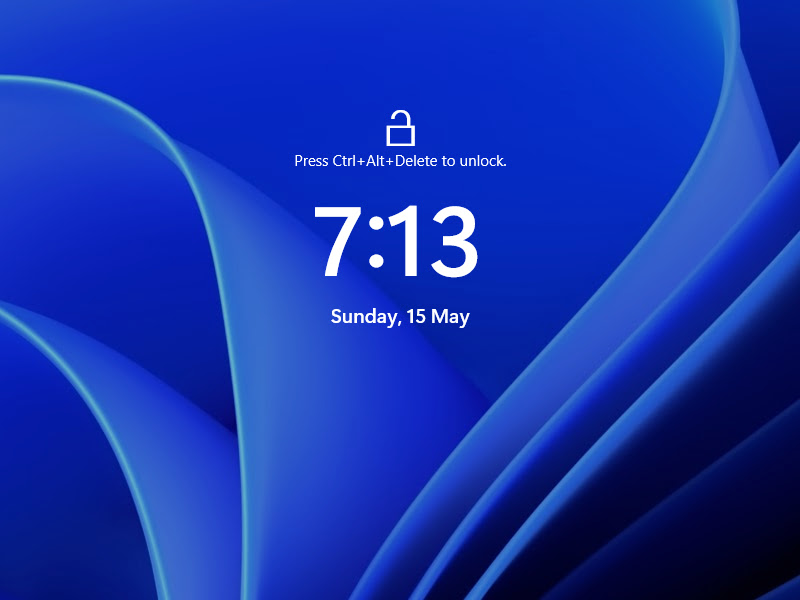
Windows 11 SAS enabled lockscreen interface
Unfortunately, as far as I am aware of, it is not possible to disable the lockscreen background. It was possible at some point on Windows 10 by modifying a registry value, but then I remember it has stopped working after Microsoft released an update. I will update this post if I ever find a way to disable it again. But until then, it will do.
References
- M. Stamp,
Authentication,
in Information Security: Principles and Practice, 2nd ed. Hoboken, New Jersey, USA: John Wiley & Sons, 2011, ch. 7, pp. 229-230. - Microsoft.
Complementary features to Custom Logon
. Microsoft Docs. https://docs.microsoft.com/en-us/windows-hardware/customize/enterprise/complementary-features-to-custom-logon (accessed May 14, 2022). - B. Bloodworth.
security - How do I remove the “Reset Password” option from the Windows 10 login screen?
. Super User. https://superuser.com/a/1537060 (accessed May 15, 2022). - P. Yosifovich, A. Ionescu, M. E. Russinovich, and D. A. Solomon,
Security,
in Windows Internals, Part 1, 7th ed. Redmond, Washington, USA: Microsoft Press, 2017, ch. 7, pp. 712.
